Industry Webinar: Active Directory A Primer for Protection
AD is a key attack point due to poor visibility and security controls - what can be done?
Active Directory is still a mainstay for many mid to large organisations, even those that have migrated key services to rely on cloud identity provider services provided by the likes of Microsoft Entra ID.
AD on-prem is still often used for syncing outbound identity data and indeed is still used for on-prem related services and application integrations for single sign on.
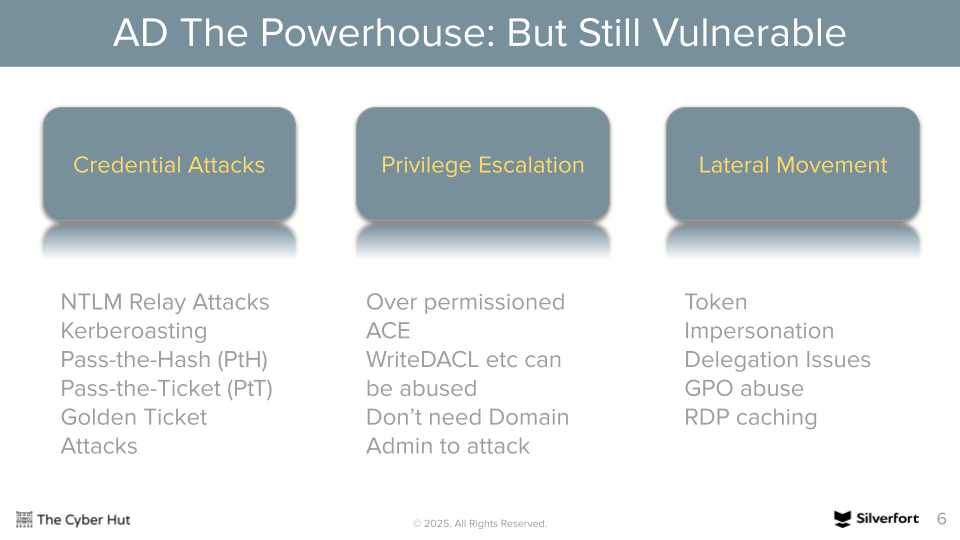
However, it is a key target for adversarial activity. Why? It is likely that many organisations support AD via an infrastructure-lens. Identity and cyber security teams may well either not be present in the organisation, leaving core AD support functions to a more general infrastructure team which could be due to organisation size or a lack of specialist personnel. AD can just often be seen as plumbing. The reliable LDAP wiring for an organisation that is essentially two and half decades old. What could go wrong? It is quite common for AD to not be seen as a security concern.
Add to this the ability for AD to essentially allow both standard employee and service account lateral movement to a range of different services and functions provides adversaries with a strong effort/reward ratio if targeting it.
The three main identity-related attack building blocks could be seen as credential, privilege or lateral movement related - albeit that is still only a snapshot.
We have seen numerous data breaches and threat attack campaign groups in recent years exploit numerous vulnerabilities within AD to great affect.
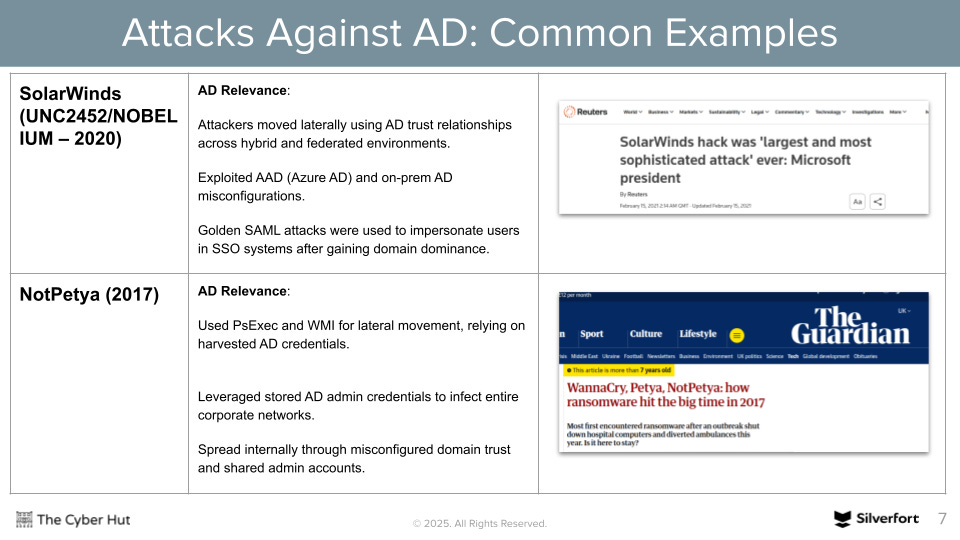
It is interesting to consider attacks like SolarWins and NotPetya - whilst not entirely just reliant on AD vulnerabilities - occurred in a time before AI was commonly adopted.
Whilst the impact of these attacks was HUGE, with millions of dollars of impact, they almost look manual in comparison to what is now possible with AI. A recent report by Anthropic shows how AI infrastructure can be used by attackers to build out more scaleable and automatic ways of performing recon, initial access and more.
Of course, blue-teamers also have AI capabilities to assist in the detection of malicious behaviour but also in the detection of data issues such as stale accounts, excessive permissions, shadow-admins, shared service accounts and the like.
Our next industry webinar will be tackling this topic in detail as The Cyber Hut’s founder Simon Moffatt will be conversation with Rob Larsen from Silverfort.
About The Webinar
Active Directory (AD) remains the backbone of most enterprise environments - and one of the most targeted systems by threat actors. Once attackers gain an initial foothold, they often move laterally across systems, leveraging unmanaged privileged accounts, invisible service accounts, and gaps in MFA enforcement to escalate access and compromise critical resources.
In this webinar, we’ll explore how to modernize your Active Directory security to meet today’s threat landscape - without ripping and replacing what you already have.
Key Topics Will Include:
How attackers exploit native AD protocols (like NTLM and Kerberos) for lateral movement
Why traditional MFA tools fail to protect many critical AD authentication paths
How to discover and secure unmanaged privileged and service accounts
Ways to extend MFA and access policies to any resource - even ones that couldn’t be protected before
Real-world use cases and practical steps for reducing identity-based risk in your environment