Cheat Sheet: MCP Security
Open source resources, articles and provider links
The What
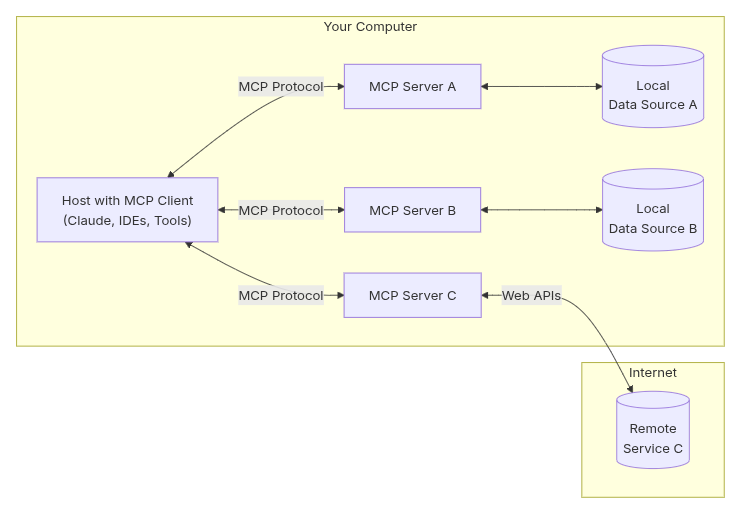
Image Source: MCP Protocol Site
“MCP is an open protocol that standardizes how applications provide context to LLMs. Think of MCP like a USB-C port for AI applications. Just as USB-C provides a standardized way to connect your devices to various peripherals and accessories, MCP provides a standardized way to connect AI models to different data sources and tools.”
The above quote is taken from the MCP protocol site. With the proliferation of large language models, MCP aims to provide some stabilisation with respect to interactions and the context that passes between the involved parties.
The Why
“MCP helps you build agents and complex workflows on top of LLMs. LLMs frequently need to integrate with data and tools, and MCP provides:
A growing list of pre-built integrations that your LLM can directly plug into
The flexibility to switch between LLM providers and vendors
Best practices for securing your data within your infrastructure”
As with any standard, the core aim is abstraction and to improve value of core systems - by not having to spend time on integration “plumbing” that often requires duplication and reuse.
The main building block components include:
“MCP Hosts: Programs like Claude Desktop, IDEs, or AI tools that want to access data through MCP
MCP Clients: Protocol clients that maintain 1:1 connections with servers
MCP Servers: Lightweight programs that each expose specific capabilities through the standardized Model Context Protocol
Local Data Sources: Your computer’s files, databases, and services that MCP servers can securely access
Remote Services: External systems available over the internet (e.g., through APIs) that MCP servers can connect to”
Considerations
The following should be considered with respect to the use of MCP within AI deployments:
Third party MCP components should be treated in the same way as securing third party software and libraries
Mutual authentication of clients, hosts and services needs to considered, designed and implemented
Authorization with respect to servers and data sources as a minimum
Confidentiality protection at the transport layer may not provide enough fine grained authentication or access control
Integrity protection of data sources
Use of end to end TLS
Egress filtering of PII/PHI
Secure handling of token material in transit, at rest and during use/validation
Consent and privacy management between end user request/prompt interaction and downstream responding systems (E.g. history, request processing)
Capabilities
The following capabilities should be considered with respect to MCP identity security management:
Access control for underlying resources and data sources
Monitoring of resources and data sources
Request and access rate limiting
Confidentiality protection for data sources at rest and in transit
Integrity protection for data sources at rest and in transit
Industry and Market Resources
The following contains a set of links from industry groups, vendors and solution providers who have published further material in this or related areas.
NB - links subject to change, not associated or endorsed by The Cyber Hut and you follow at your own risk.
Industry Articles:
Anthropic: Introducing the Model Context Protocol
AWS: Open Protocols for Agent Interoperability Part 1: Inter-Agent Communication on MCP
AWS: Open Protocols for Agent Interoperability Part 2: Authentication on MCP
MCP-Scan: An MCP Security Scanner (Open Source)
MCP-Watch: Comprehensive Security Scanner (Open Source)
Enterprise-Grade Security for the Model Context Protocol (MCP): Frameworks and Mitigation Strategies
Microsoft: Understanding and mitigating security risks in MCP implementations
NCC Group: 5 MCP Security Tips
SGNL: Securing MCP servers
Silverfort: Beyond the hype: The hidden security risks of AI agents and MCP
SecureAuth: Wiring MCP to Your IdP
SemGrep: Security Engineers Guide to MCP
WhatsApp MCP Exploited: Exfiltrating your message history via MCP
Industry Frameworks:
Vendor Solutions:
Auth0: MCP Server
Britive: Securing MCP Workflows: Dynamic Agentic AI Access Control
Omada: Advances AI-Ready Governance with the Model Context Protocol Initiative
Saviynt: MCP Server for Identity
SecureAuth: How to Build a Secure AI Agent Using SecureAuth and MCP
SGNL: MCP Control Plane
Teleport: MCP Infrastructure Security
Token Security: NHI Based MCP Server
Trail of Bits: MCP Context Wrapper
Last Updated: Dec 3 2025. Email info@thecyberhut.com for additions and errors.