From Defending Resources to Pathways
From Defending Resources to Pathways
The last 3 years has seen a significant change in the way the “bad guys” attack and how organisations defend against malicious attacks - specifically attacks that originate externally to the organisation.
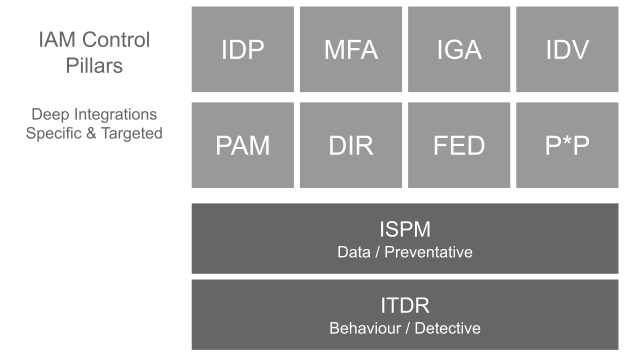
Many mid to large size organisations across many sectors, invest upon the main pillars of identity and access management. So we’re talking about identity providers (IDP) for both internal and federated inbound authentication. In addition, the IDP gets wired into as many downstream systems as possible - ideally via standard protocols (think OIDC, SAML) but also proprietary cookies, proxies, gateways and the like. The TLDR; is that the IDP is not something that get’s replaced frequently. Think 3-7 years lifespan.
Image Source: The Cyber Hut market guide on ISPM
But the IDP needs to adapt, so gets augmented by strong authentication options, multi-factor authentication, passworldess, passkeys and the like. To trigger those modals, we then add in risk-based authentication, adaptive authentication, contextual authentication and other terms that essentially refer to the fact the authentication needs more information to help make better decisions. That information could be related to the device, location or external threat intelligence sources.
Organisations also invest heavily in identity governance and administration (IGA). So access request, access review, roles stuff (creation - role mining, recovered from that yet? - role management, SoD checks etc) which relies upon provisioning and off-boarding workflow management systems. Sometimes they’re separate, more laterally integrated. We then see privileged access management appear - and somewhat paradoxically - often managed by teams outside of the traditional IAM operational boundaries.
So we have IDPs, MFA, PAM and IGA and dependent on maturity, systems under management and the like, we also see some external policy based access control (PBAC) authorization platform in the mix too.
And guess what? Organisations still get breached. Again. Still. You can Google that.
So what is happening? Well we have historically thought about both security controls and often the IAM fabric in terms of resource-centricity. The budgets for PAM, SSO, governance and access control were all likely separated - both operationally and financially. Different metrics, ways of integrating and ways of discovering the benefits and issues.
The bad guys - remember those - they don’t care. They don’t care those tools are not managed by the same team. That their logs are not integrated. That the systems they cover do not overlap. That the sessions between them are unrelated. That identifiers are not correlated effectively.
The bad guys think in terms of flows. Information flows, access paths, journeys. They want to get hold of an object. A piece of data (or huge amounts of), a transaction, an API under protection and so on. How they do that, is unrestricted to them. They are not having to think about compliance, operational boundaries and ticketing systems. They are like water and will find the quickest, most direct route to the object they want to access.
To that end we are seeing the huge rise in information pathway analytics capabilities. Many fall into the “identity threat detection and response” ITDR bucket and don’t always use the same terms.
Access Path
Information Flow
User Journey
Journey Analytics
Event Chaining
Session Analysis
The main capability though, is to provide a visualisation approach (likely graph and pivot-able via the identity, not just the resource, device, IP or network) that links the IDP, relying party, app-level activity and overlaid with threat intelligence, techniques, tactics and procedures to pop out a risk value.
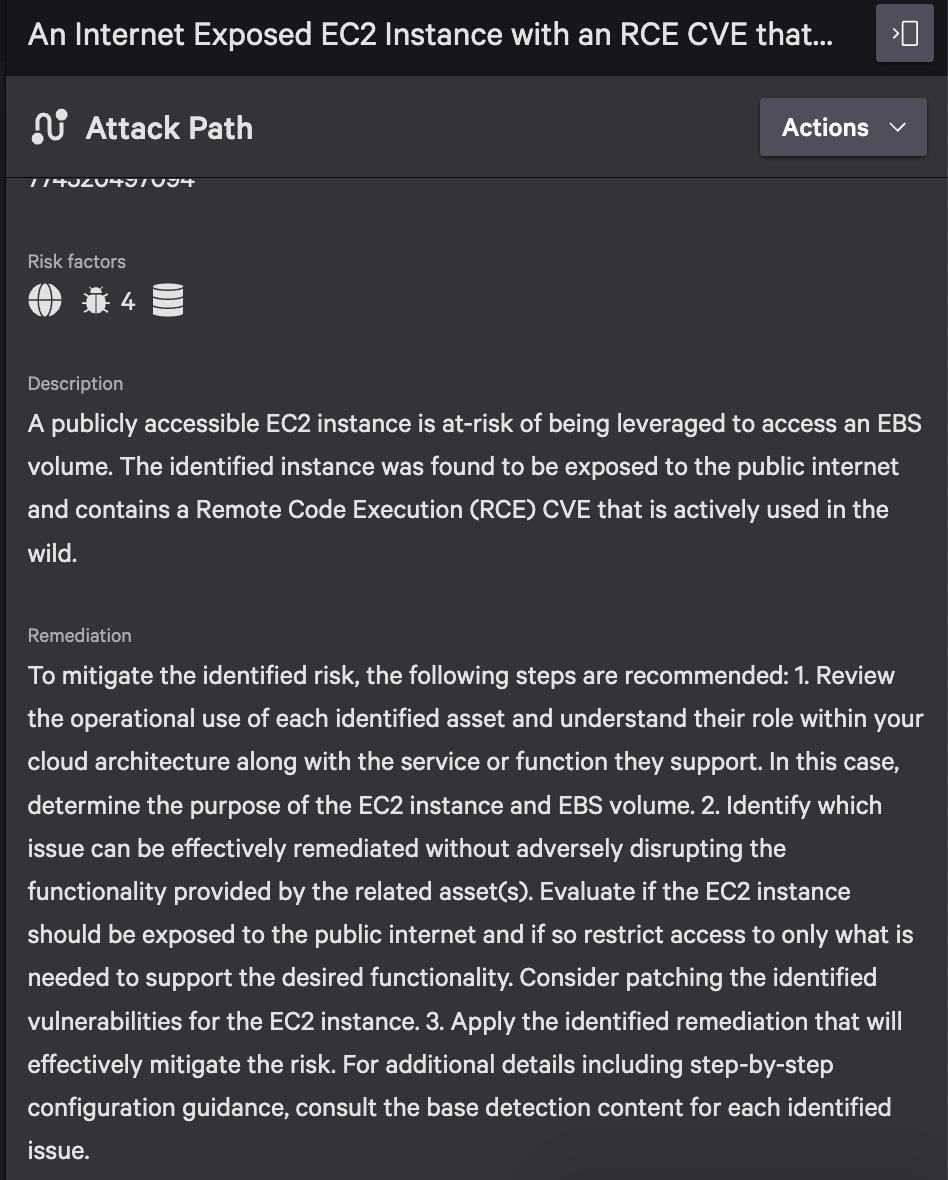
Image Source: Crowdstrike blog on Sensitive Data Tracing
The above image is from Crowdstrike, by many other vendors such as Silverfort, Breez Security, Permiso, Sharelock, Hydden, Unosecur, Authmind and Reveal Security aim to deliver capabilities in a similar way. And more importantly provide recommendations for remediation.
This is a somewhat historically different approach to defending the information assets in an organisation. We augment the individual pillars of control (which are still essential I hasten to add) to a more end to end way of both detecting and in turn responding and remediating the threat.
More systems come under the visibility eye as well as supporting the ability to respond in a more variable and fine grained way - from terminating sessions, to dynamically removing access - diverting to deception systems and ultimately changing policy to prevent future attacks.
This is a systemically different way to protection. We’re moving away from resources to an overlay and platform-centric approach. This becomes target system agnostic as well as being inbound authentication event agnostic.
I didn’t mention AI yet (drink!) or non-human and agentic-AI related identities. They too will need this access path model applying to them.
Both the runtime monitoring and data management aspect is moving to being end to end, overlay and in a separate and powerful way to augment the existing IAM capabilities.
Quick Pick Vendor Updates:
1Kosmos: What the Marks & Spencer Breach Tells Us About the Next Era of Identity Attacks
Axiomatics: Agentic AI and NHIs: Why authorization is a must-have
Crowdstrike: Tracing Attack Paths to Sensitive Data in the Cloud
CyberArk: The quantum-AI collision: What CISOs must do now to stay ahead
FushionAuth: Welcomes New CEO Brian Bell to Lead Next Phase of Growth
Gathid: Beyond Firewalls: How to Fix Identity Gaps In Operational Technology
Google: Just say no: Build defense in depth with IAM Deny and Org Policies
Kaspersky: Passkeys in 2025: tips for power users
Orchid Security: Learning from the Past is Great, Preparing for the Future is Even Better
Sailpoint: Machine Identity Growth
SecureAuth: White Paper: Identity 101 for AI Agents
Veza: Better Together: Augmenting SailPoint with Full-Stack Access Visibility
Identity Threat Intelligence Updates:
Up Coming Industry Webinars:
Addressing the IAM Data Problem: A fireside chat with Radiant Logic, July 22nd
Up Coming Conference Attendance:
IAM Tech Day - Porto - Sept 23
The Identity Underground Summit - Denver - Oct 6/7
Latest Research Report:
The Cyber Hut: A Market Guide to Identity Security Posture Management (ISPM): The Role of Data-Centric Identity Observability
Recent Insight and Comment:
Interview on Ep. 118 Identerati Office hours sponsored by Gluu (Future of IAM)
Interview in Issue 02 IAM360 magazine by Thales (The new meaning of identity)
Cheatsheet: Agentic-AI Identity Security
Evolution to Detective Identity Security
Trusted Computing: Emergence of a Vital Sector
Recent Industry Webinars
An Identity Security Playbook: The What and The Why with Silverfort
Putting the AI in IAM a fireside chat with Apono
Recent Academy Episodes:
Recent Vendor Introduction Interviews:
Recent Podcast Episodes:
The Voice of Industry: Interview with Liv Horan IAM Recruitment Specialist
Order Recent IAM Books on Amazon:
IAM at 2035: A Future Guide to Identity Security - Paperback, Audio, Kindle and Hardback
CIAM Design Fundamentals - Paperback, Audio and Kindle