How To Design for Continuous Identity
Identity and the systems and data that make identities effective, productive and secure are not static. They are constantly in flux - changing to business objectives, external cyber threats and strategic aims.
When commercial identity and access management systems become popular in the late 1990s they were focused on linear use cases such as single sign on or access review for high risk systems. The design of technical features and the overarching workflows were often done in a waterfall approach - with lots of effort up front, and very little spent on day to changes and how the IAM functions could respond to external events.
In a previous opinion piece, I also amplified how the classic joiner-mover-leaver process was not built with security in mind - it was built with productivity as the main driver and in turn is often the target of adversarial effort.
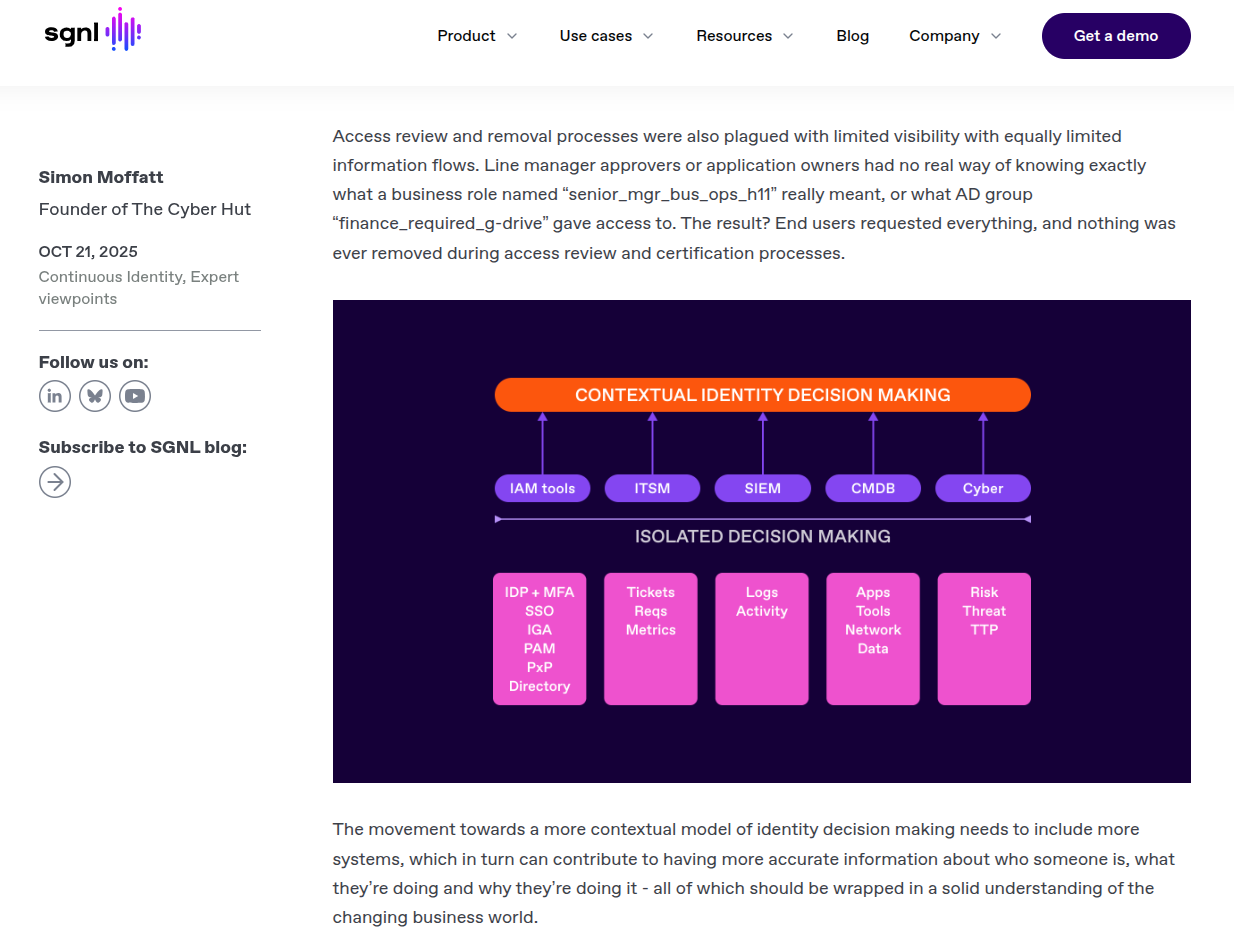
A movement to something more continuous, requires a deeper and broader integration of the IAM fabric to other systems - systems that help with gathering more context, balancing out the information asymmetry problem and aiding with decision making under limited knowledge.
These systems of course likely already exist within the mid to large sized enterprise - ticketing systems, configuration management databases, logging systems, cyber threat intelligence and security operations can all provide vital signals that can assist in an array of IAM decision making.
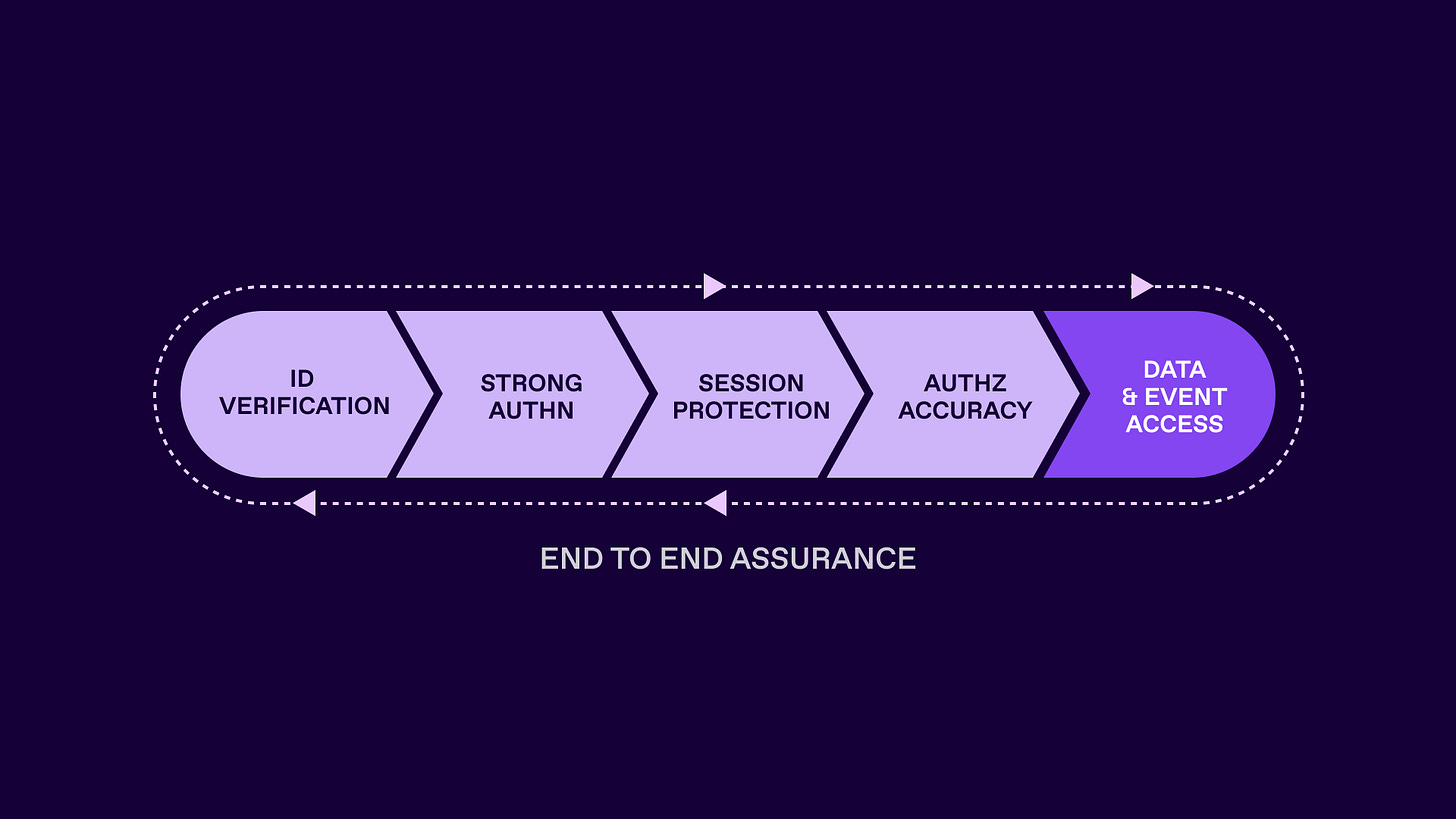
That is how to focus on both the existing static limitations and benefits a more dynamic approach can bring: the decision making limitations. Where in the IAM life cycles of both data and runtime behaviours, are decisions difficult?
Access request
Access review
Access enforcement
Session evaluation
Access removal
The above are just some examples where analysis and decision making is restricted - at best coarse grained - at worst guess work.
More data is one thing, but getting that data at the right time is also part of the strategic shift. Risk signalling is becoming a key part of the security world where session evaluation and access enforcement stages can be enhanced with information pertaining to device issues, location or cyber threat intelligence relating to a specific tactic or behaviour.
But getting that information after an event has been evaluated is not much use. Getting extra signals prior to the time of evaluation is key.
Concepts like the Shared Signals Framework can be one part of that design pattern - providing a standards based way to get new signals from a traditionally disparate set of sources. This can increase assurance to a broader set of downstream services expanding on the key assurance concepts applied to identity profile creation and authentication verification.
In a recent article for SGNL, I expand upon these concepts in more detail and describe what is needed and what benefits it can bring.
“So what does a more contextual identity decision making model achieve? By simply improving the asymmetric information problem we can instantly start to be more targeted with respect to risk analysis and treatment. Not all identity risk is the same and a major concern for many organisations is they treat all identity related issues with the same level of priority - simply as they do not have the information to make more informed decisions. As organisations also struggle with alert-fatigue within the retrospective and reactive security operations world, being both proactive and focused immediately improves an organisation’s identity risk posture with appropriate identification and treatment options.”
About the Author
Simon Moffatt has nearly 25 years experience in IAM, cyber and identity security. He is founder of The Cyber Hut- a specialist research and advisory firm based out of the UK. He is author of CIAM Design Fundamentals and IAM at 2035: A Future Guide to Identity Security. He is a Fellow of the Chartered Institute of Information Security, a regular keynote speaker and a strategic advisor to entities in the public and private sectors.