If Continuous Identity is the Answer, What is the Question?
Why stale access means stale risk management
We as both people and employees and the associated identity and account infrastructure needed to allow us to perform, does not stand still. We are not static and we don’t operate in a static environment. We often perform multiple different roles simultaneously, seamlessly switching across teams, projects and responsibilities.
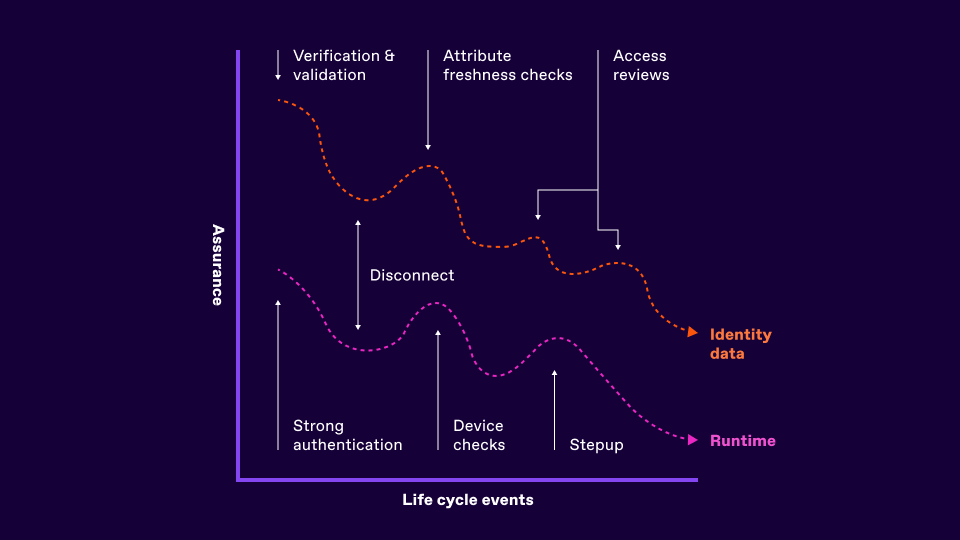
Yet both the identity data and identity runtime ecosystems that are needed to represent our B2E interactions digitally often standstill - with static or point in time checks, processes and controls.
Verification and validation stages performed when an employee joins an organisation are often not revisited until perhaps an audit or yearly review - if at all. Authentication events - such as step-event events triggered by “high risk” are often only delivering high assurance for a few seconds or minutes after they complete.
Why is this relevant? Well our digital world moves incredibly quickly - and must incorporate risk, threat intelligence, business process and business needs simultaneously. Our identity and access management infrastructure really needs to mirror these realities - and in turn be more continuous and responsive.
In the first of a three-part series, The Cyber Hut founder Simon Moffatt, wrote a guest blog for SGNL outlining the rise of Continuous Identity - what it is and what it’s needed.
“Simply put, the joiner-mover-leaver process was not designed to support assurance and security from the offset. It was designed to improve productivity and reduce costs - with compliance being an optional add-on to rectify market failures for those in regulated industries.”
As the modern enterprise needs to deliver productivity for staff, security and zero trust architectures, remote access and of course compliance, the underlying IAM infrastructure has an increased responsibility to be integrated against more systems, and orthogonal technologies than ever before.
With that responsibility comes the need to deliver assurance at both the data and runtime level that accurately reflects both the risk and threats the IAM infrastructure faces.
“Network, SASE, endpoint and data security tools assume the identity layer can self-discover, react to data and contextual changes, onboard new systems rapidly and be event driven. Onboarding a new SaaS application should not be slowed down by poor IAM. Cyber threat detection should not have the recovery stage impacted by poor IAM. Changes to data classification tags should be accessible immediately and not be reliant upon hours or days worth of IAM changes.”
These external systems expect functional and non-functional capabilities that discover, analyse and respond to risk and external events dynamically - without complex workflow or change events.
Organisations must consider how they can both integrate IAM to more systems, consume more contextual information to make more informed access decisions but also develop IAM capabilities that are responsive.
Read more on the full article here.