Industry Webinar: Discover, Protect, Defend.
Threat detection across humans and non-humans
Identity and access management has become not only a strategic enabling technology that supports productivity improvements, risk reduction and revenue generation, it has also become the number one attack surface for adversarial activity.
Be that external attacks that are motivated by financial or intellectual property gains, insiders looking to steal secrets, or accidental security mistakes due to poor policy – identity vulnerabilities are being exploited.
Our IAM world of course is not just limited to staff, contractors and customers. We also need to consider non-human identity – from services and workloads to the more recent emergence of agentic-AI. These non-humans need management too – from governance and on-boarding, through to strong authentication. Getting this wrong will be exploited.
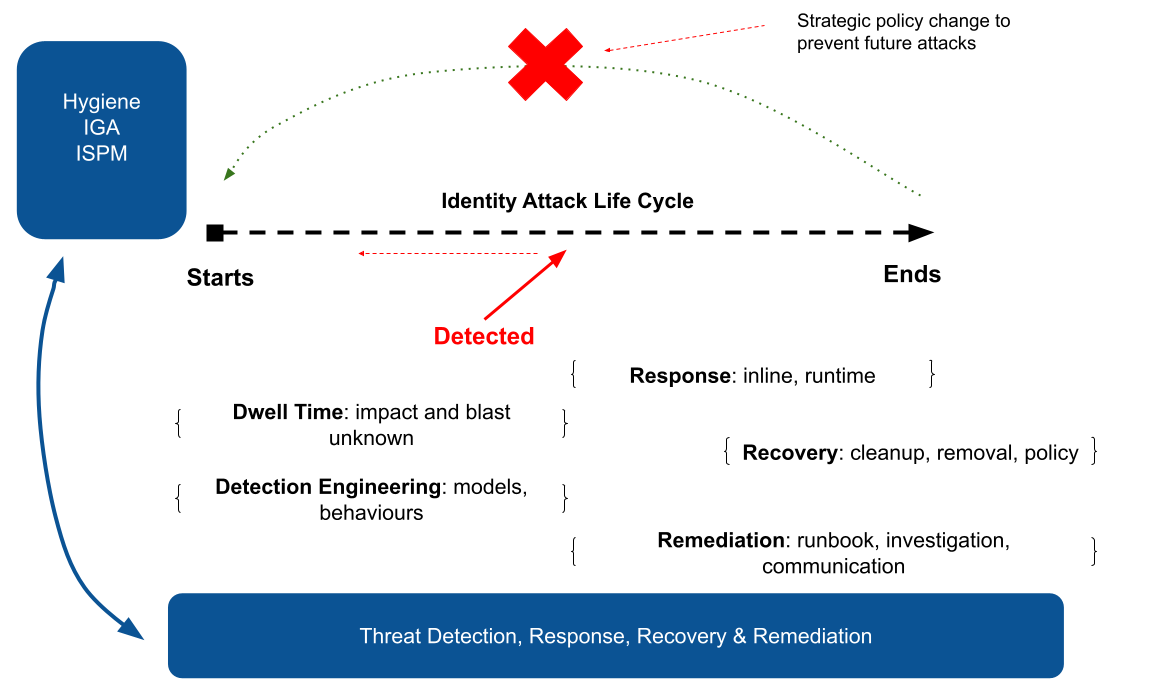
I have talked before about identity attack lifecycle management and the various emergent ways we can now tackle threat. This typically involves thinking in two lateral lanes above the core IAM infrastructure - namely identity data and identity runtime activities.
It is becoming increasing important to be able to track identity behaviour post login across a range of downstream systems that are now being rapidly integrated to the identity world. The idea of course, is to stop attacks before they happen - but many would settle for stopping them before they complete. That is a subtle difference but a good starting point. Organisations have often been left with post-incident analysis effort - the retrospective “looking at logs”. If it’s in the logs, it’s already happened and maybe too late.
Detecting and responding to some sort of identity threat as early as possible is obviously key. But it also important to understand that the “threat” needs to be considered across different identity types (customers, partners, employees, workloads and agents..) and at different parts of their respective lifecycles - from onboarding, directory storage, authentication, credential management, session issuance, authorization enforcement and so on. This introduces a lot of moving parts and unfortunately multiple avenues for adversarial activity to potentially go unnoticed.
Our next industry webinar will be next week (Sept 17th) where The Cyber Hut will be conversation with Permiso Security to uncover some of their deep dive research on the most recent and insidious identity attacks - taking in Scattered Spider, phishing attacks on Microsoft Teams, remote employee fraud attacks and the latest on Salesloft.
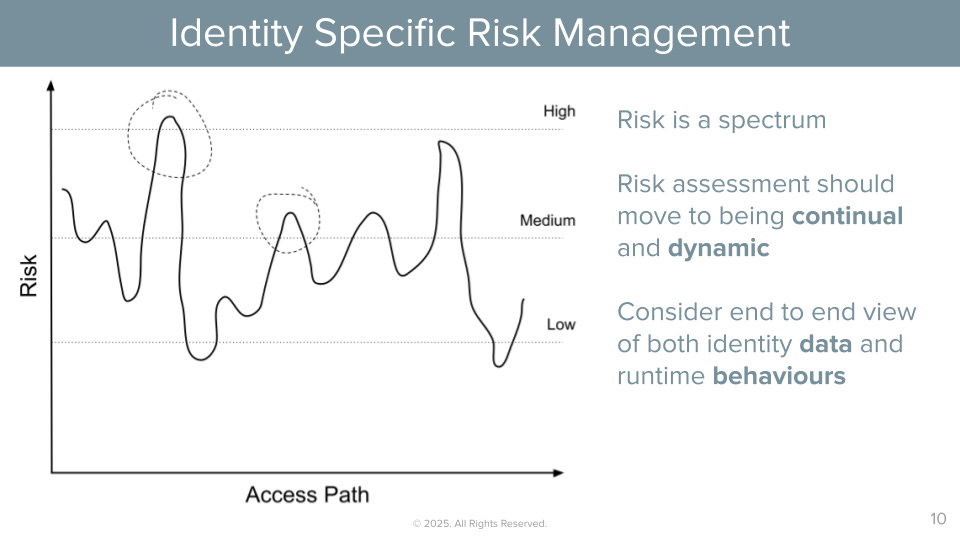
Risk associated with identity and access paths and their flow towards objects and data is constantly in flux and can’t be handled effectively with static point in time controls or one of enforcement options.
Join us in this webinar to discuss:
How a more holistic, human and non-human identity-security strategy can help
How to detect, protect and defend against emerging threats
The need for discovery, analysis and remediation across human and NHI
Deep dive examples on recent threat exploits, their attack patterns and detection methods.