Review of Black Hat Europe 2025
Leading security vulnerability research event hits London
This week I had the pleasure of spending two days at the Black Hat Europe 2025 event at the Excel exhibition centre in London. The unseasonably mild weather, whilst knocking the edges off the Christmas spirit, added a bright and light feeling to the venue
I attend BH most years and I would say this was the biggest turnout for London - but I don’t know the official numbers just yet - they’ll be announced next week. Close to 4000 I would estimate (NB the official BH press release stated 4500). This is a premier security research and vulnerability disclosure event with some exceptional contributions from academia, consultancy and individuals. The vendor exhibition area is gathering a broader array of vendors and sponsors, with the arsenal section (featuring open tools and accelerators) is always an eye opening look into what is being codified.
TLDR; takeaways: AI is a concern for many. How to protect, how to build with, how competitors and malicious operators are adopting it and what is means for productivity and security in general. The core food for AI is data - and that requires confidentiality, control and integrity protection. Of course, the building blocks of security shouldn’t - and weren’t - ignored, with many tools, talks and products aimed at optimising age old issues like AD security and backup, credential vaulting and code issue discovery.
Key highlights included:
Day 1
China‑Nexus APT Exploiting Ivanti Endpoint Manager Mobile
First up on day one that caught my eye was a talk looking at the MDM space by Arda Büyükkaya from EclecticIQ, a threat intelligence platform provider. The talk discussed how the Ivanti MDM platform had been exploited - which essentially allowed unrestricted access to the mobiles under management - including access to install apps silently, ability to remote wipe, gain access to session and token material and some PII. A zero day was exploited with some memory dumping of Java and Tomcat running processes leading to exposing of DB credentials. Lateral movement was via reverse proxy with many victims in the EMEA region. Essentially a not-so subtle supply chain attack via a commercial platform, utilising a nation-state style zero day exploit. This concept of attack is becoming increasingly difficult to defend against it seems.
Slashing QUIC’s Performance With A Hash DoS
Paul Bottinelli from the highly respected Trail of Bits did a deep dive talk on a vulnerability within non-cryptographic hash functions that are often used for indexing purposes when storing key/value data pairs in various languages. He took a complex topic and very clearly explained the issue behind how a combination of weak hash algorithm implementation coupled with attacker controlled inputs can essentially result in host denial of service - due to data processing constraints. Collisions are effectively created when pushing data into a table that results in multiple entries for the same index position - which takes server side effort to maintain. He showed how the quic protocol (which is popular due to being based on UDP and in turn reducing the TCP and TLS handshake steps) is vulnerable to this approach.
Exposing Lives and Devices Behind Encrypted Doors
Continuing the cryptographic theme, an afternoon session saw a talk more grounded in academic research from the Eindhoven University of Technology as well as researchers from Bitdefender. IoT in the consumer space has exploded in the past 10 years. I was involved in some of the IETF Device Authorization spec work about a decade ago, that is now used to pair smart TVs and sports goods to user profiles. The aim was to improve interop and connectivity. Move on 10 years and the Matter protocol was launched a few years ago to improve both security and user experience from a slightly different angle. Whilst Matter prescribes secure encryption algorithms and their modes (think AES128-GCM) it is also seemingly quite rigid - with a very structured messaging design and limited handshake options (which reduces agility and swap out potential). Alas, whilst confidentiality for now may be improved, the talk took a detailed look at privacy.
Traffic analysis could result in device behaviour leakage as well as taking a stab at understanding how many people reside in a building for example based on things like motion sensor triggers and the like. A lack of uniform packet size was the main culprit amongst others. Privacy regulation such as GDPR whilst raise awareness are not detailed in how to handle things like payload design and traffic analysis protection. A fascinating piece of research.
Surviving Identity Attacks: Don’t Become Tomorrow’s Breaking News
A sponsored session by Rubrik (who position themselves as data security specialists with a splash of identity resilience) delivered a sponsored talk in the exhibition area. They built a nice narrative around how attacks are moving away from malware to the credentials - as “identity is the new perimeter” to quote a nice buzz phrase. Whilst the IAM world always knew this and designed accordingly, the data and network worlds on the back of zero trust swap-outs are catching up too. The talk essentially was telling us what Rubrik are finding out about IAM - namely AD is still in situ for many, and that it’s a key adversarial target (NB see the recent industry webinar The Cyber Hut did in December with Silverfort on AD Protection Against Lateral Movement and Privileged Access Abuse).
They continued the narrative by focusing on how to recover AD in the event of an inevitable attack - with secured backups that can be accessed and utilised in the event that the original AD being unavailable. They didn’t touch on the fact of how to then improve the original AD security posture to prevent the same attack unfolding again.
Day 2
From Script Kiddie to Cyber Kingpin: Preventing the Predictable Progression
The morning keynote on day two was the BBC’s cyber correspondent Joe Tidy. He has recently released a new book entitled “Ctrl+Alt+Chaos” analysing cyber attacks based on teenage hacking activity over the past 15 years. It was quite a high-level walk through some of the key attacks and personalities that have emerged in the past decade or so and the names behind the Twitter handles. Whilst a frothy narrative approach outlining “the how”, the talk didn’t really do any great analysing of “the why”. The why really needs to map into some of the basic psychology and personality disorder building blocks such as the levels of Openness, Conscientiousness, Extraversion, Agreeableness and Neuroticism. Whilst analysing victims provides a retrograde approach for protection, a deeper conversation needs to be had about the why. (Disclaimer I have not read the book, which may well provide this).
Cryptanalysis And Reverse Engineering Of Letter Sealing
Further on Thursday morning was a great talk taking a look at the LINE app - that is hugely popular in south east Asia. The talk focused on the fact the app aims to deliver end to end encryption (E2EE) for both one to one and group messaging - which they identified wasn’t as secure as they thought. Whilst some key features to support this existed - namely session key derivation using ECDH - some issues existed with regards the group key management piece - which could result in the ability to listen to group chatter you are not part of and and manipulate replay and ordering of messages too.
They also highlighted some privacy issues with respect to the use of stickers within the chat functionality - in the fact things like user-agent strings were being exposed that could potentially identify users - which may be quite interesting if political or socially significant events were taking place that relied on specific use of stickers.
They ended by explaining that “double-ratchet” approaches to key generation (that essentially continually generate per-message keys) used by the likes of Signal is likely the way to go for these type of use cases.
Unmasking Organizations’ Security Postures: Insights From Phishing-Resistant Authentication
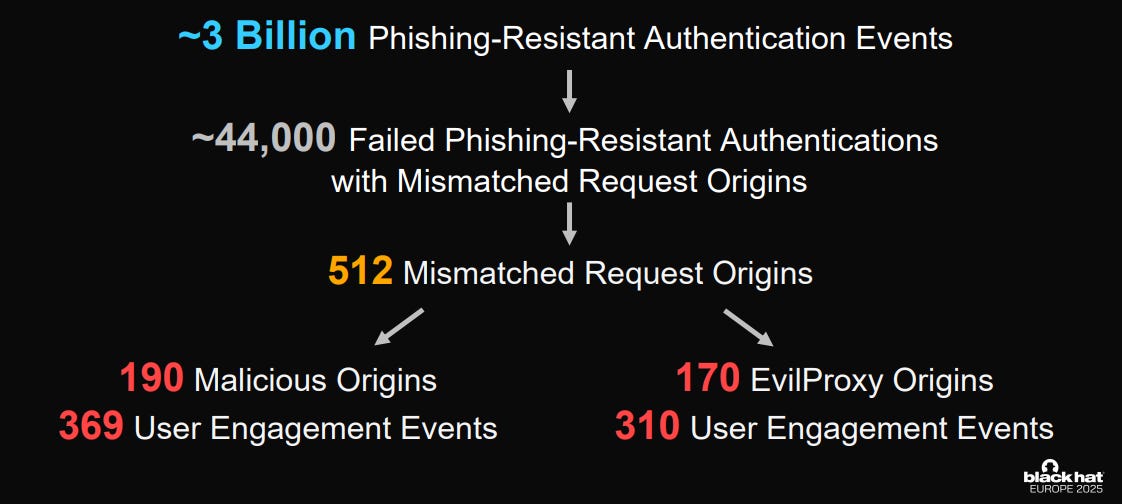
A late morning talk tackled something many organisations are aiming to deploy - that of phishing resistant authentication. This was presented by Fei Liu a principal security researcher at Okta. The presentation was a very clear and excellently structured talk looking at an 18 month period of authentication-event data collection and analysis - covering a healthy 3 billion events.
Origin-binding is the main premise for phishing resistance, but of course social engineering and well crafted emails and websites can overcome this. Tools like EvilProxy accelerate this attack process.
Image Source: talk by Fei Liu
A structured approach to finding out if domain mismatches were occurring during authentication was used to identify whether something malicious was happening - or perhaps a legitimate issue.
The end result, was that phishing attempts are highly likely - and protection requires both a pre-auth and post-auth approach.
Who Gets to Point Fingers? Technical Capacity and International Accountability
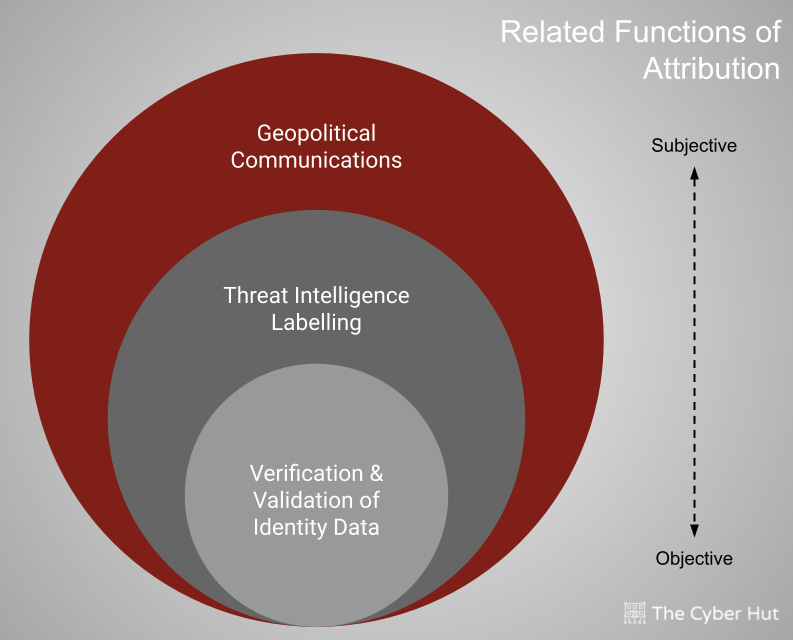
Attribution is becoming a key theme in post breach analysis with numerous threat intelligence platforms and research providers often competing to name campaign actors and groups - and in turn relaying indicators of compromise and detection steps to the community. However there are a couple of other angles to consider.
One is the lower level identity attribution process (which needs to include people and non-humans, based on verification and validation of profile data along with biometric overlay) and that of nation-state and geopolitical use of attribution as a lever in statecraft. This talk was on the latter and what this actually means in the growing role of hybrid warfare and grey zone dynamics.
Image Source: The Cyber Hut
I wrote about the future considerations for identity security in IAM at 2035 which needs to consistently fulfil both the attribution and intent analysis functions in a repeatable way for all identity types. My focus was on the lower level triangulation of identity data and authentication events - which is crucial to support the understanding of the intent behind a particular set of events. Only with a structured analytical approach to these steps can higher notions regarding malicious behaviour tied to motive and opportunity be explored.
Louise Marie Hurel - a researcher at RUSI - delivered a very well constructed afternoon keynote analysing the recent evolution in the geopolitical use of attribution as a measure of statecraft. Of course the two questions we should always be considering are the “why” and the “how”. The how can very well be normalised with technical capabilities and proof of objective analysis. The “why” behind a nation finger-pointing is much more nuanced. The talk identified how countries like Singapore and China have recently started naming and shaming intrusion events - perhaps at the expense of cultural norms. The confusion and interrelation between cyber and kinetic military attacks is becoming more so - with the contributing factors of both becoming difficult to measure.
The talk concluded with some initiatives focused on building a global model for responsible cyber behaviour which may exist outside of the UN, which may help to both define attack severity and implication as well as what and when to attribute.
AI Agents at Runtime: Stopping Misbehavior Before It Becomes a Breach
A sponsored talk by Capsule Security tackled what many organisations are worried about currently: agentic-AI. What it is, where it is and how it can be controlled. Firstly it is important to realise that not all AI is the same, and not all agentic-AI is the same. There is a matrix of both home-grown versus SaaS consumed agentic-AI versus managed and shadow. I would imagine the shadow aspect is considerably larger than many organisations currently realise.
Capsule gave a mini-demo to highlight their process - namely discover (including that pesky shadow stuff, that although may well not be controlled nor secured, is likely delivering some sort of productivity hit), observe what the agents are doing, protect the process and detect future bad stuff when it happens.
They referenced the very fresh OWASP Top 10 for Agentic Applications (a separate analyst comment is coming on this shortly) and identified three key entries in the top 10 that they aim to help solve - namely AS101 goal hijack, AS102 tool misuse and AS103 identity and privilege abuse.
Lots can and will go wrong with agents. Capsule are one of many vendors looking to secure this landscape.
Arsenal Emerging Tools Shout Outs
A highlighted mention to some interesting tools that I caught a demo of:
ThreatShield – The Intelligent Way of Threat Modelling
Raising BloodHound Attack Paths to Life
DICE: Device Identification and Classification Engine
Securing Secrets from Dev Machine to Deployments Using SLV
SkyEye: When Your Vision Reaches Beyond IAM Boundary Scope in the Cloud
EntraGoat - A Deliberately Vulnerable Entra ID Environment
Golden dMSA: One Key to Rule Them All
SAMLSmith
OWASP EKS Goat: Hands-On AWS EKS Security
Vendor Shout Outs
Capsule Security - “Capsule is securing smarter, safer collaboration between Humans and AI Agents. Be the first to see how we’re changing the game.”
Kontext.dev - “Kontext unifies app/agent access to APIs, data, and tools across identity providers. Declare who can call what with which scopes; Kontext issues the right tokens on demand.”
Push Security - “Browser-based detection and response. Powered by research.
Trusted by security teams doing serious work.”
Roseman Labs - “Roseman Labs makes it fast and easy for organizations to work together on sensitive data to generate Trusted Collective Intelligence - without giving up control, and in full regulatory compliance.”
Rubrik - “Accelerate your AI transformation. Monitor your agents, enforce guardrails, and remediate unwanted actions on one platform with Rubrik Agent Cloud.”
Smallstep - “Smallstep solves the other half of Zero Trust by securing Wi‑Fi, VPNs, ZTNA, SaaS apps, cloud APIs, and more with hardware-bound credentials backed by ACME Device Attestation.”
About The Author
Simon Moffatt has nearly 25 years experience in IAM, cyber and identity security. He is founder of The Cyber Hut - a specialist research and advisory firm based out of the UK. He is author of CIAM Design Fundamentals and IAM at 2035: A Future Guide to Identity Security. He is a Fellow of the Chartered Institute of Information Security, a regular keynote speaker and a strategic advisor to entities in the public and private sectors.