Review of IAM Tech Day 2025 Porto
I had the pleasure of being asked to keynote the first IAM Tech Day for Europe this week in the beautiful city of Porto.
The IAM Tech Day series have run multiple events over the past 5 years both on line and physically in Brazil with a community of several thousand attending their 2-day event.
My talk was entitled “IAM T+10” - IE where will identity and access management be heading to 10 years from now, based on my latest book “IAM at 2035: A Future Guide to Identity Security”. Of course no one really knows the answer to that, especially not with the rapid advances of AI, altering supply chain, economic market conditions and outside influences such as geopolitics and nation state cyber threat.
However, we can start to build frameworks of analysis that help us to understand both the business and technical challenges that currently exist and how they are starting to evolve.
Not only has IAM become strategically more important that it was say a decade ago, as we have more identities, more types of identities and more responsibilities to manage. IAM needs to integrate to more technologies and support a set of key metrics to articulate the benefits it is bringing. To add to these challenges we also have AI.
I have discussed on numerous times during 2025, the rise of AI in the IAM - both from an accelerator point of view to help with concepts such as policy design, assign names and descriptions to roles and groups, find owners for NHIs and recommend which permissions to remove for example.
But we also have to consider how to protect our AI world - from a data confidentiality, data integrity and access control point of view - all of which place huge requirements on IAM.
Some recent resources from The Cyber Hut on IAM and AI:
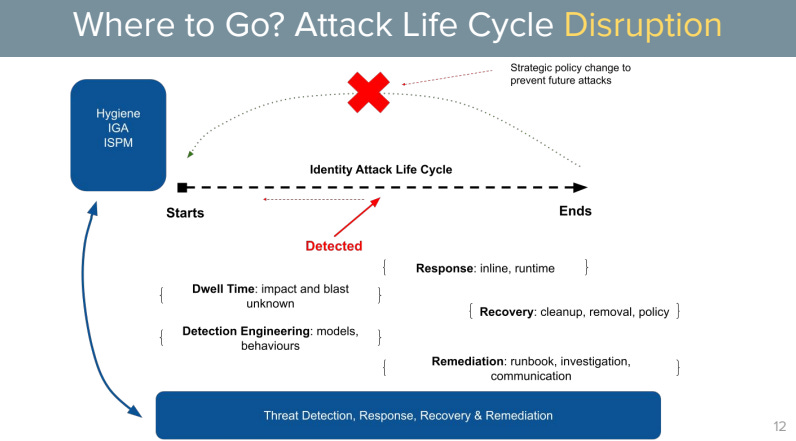
The net-net is that organisations have more identities to manage and more systems to integrate - yet existing technology stacks are often leaving gaps, blind spots and coverage concerns that create multiple vulnerabilities across this IAM infrastructure. IAM is becoming the number one attack vector for criminal and nation state activity.
So suddenly IAM becomes part of the attack life cycle and measures at both the identity data level and also the identity runtime and behaviour level need to be addressed.
Some recent resources from The Cyber Hut on IAM Data and IAM Behaviour:
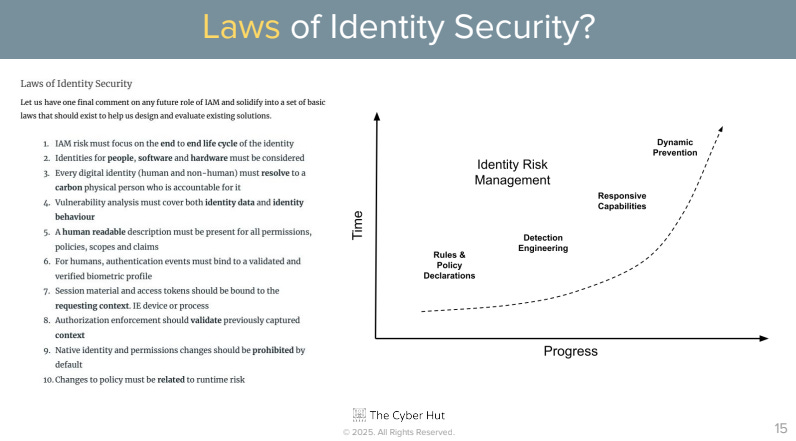
My talk continued with a discussion on a potential set of 10 Laws of Identity Security - what that entails and how we can start to evolve both our thinking and also architecture to protect our IAM assets and that technologies we will have at our disposal in the next decade to tackle many aspects of this.
The rest of the day continued with a range of talks from vendors, end users and advisers covering an array of IAM concerns from IGA to attack path analytics for machine identity.
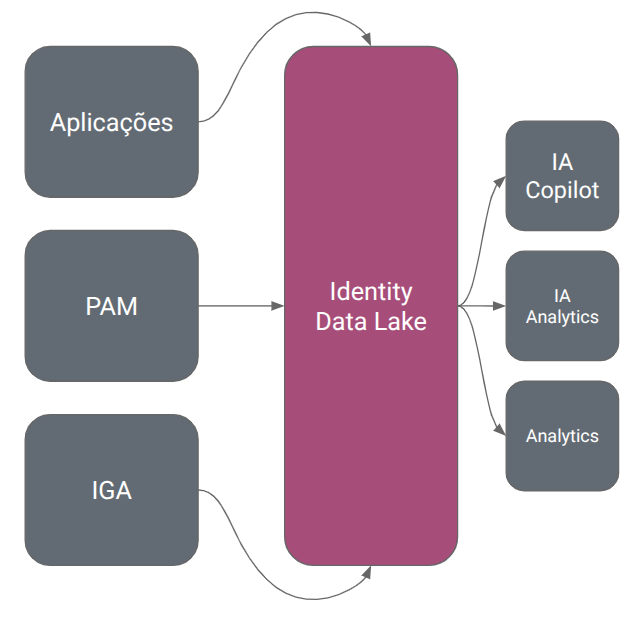
Alfredo Santos discussed the need to improve orchestration approaches for identity governance and administration and amplified the now popular concept of Identity Data Lakes - centralised approaches to understanding the underlying landscape in order to remove excess permissions and find risk more simply. He concluded they will be continued convergence between the likes of PAM, IGA and CIEM - something The Cyber Hut discussed last year.
Vendor presentations included Manage Engine, RSA, Okta, AuthCube, Ping Identity and Sailpoint.
Mohamed Zohny from RSA had a short acronym for their approach - the 3 P’s of “Passwordless, Platform and Posture”. Ultimately organisations want to save money, improve security with a zero trust approach (of which IAM is foundational) and apply tactical controls such as passwordless authentication and hygiene improvements.
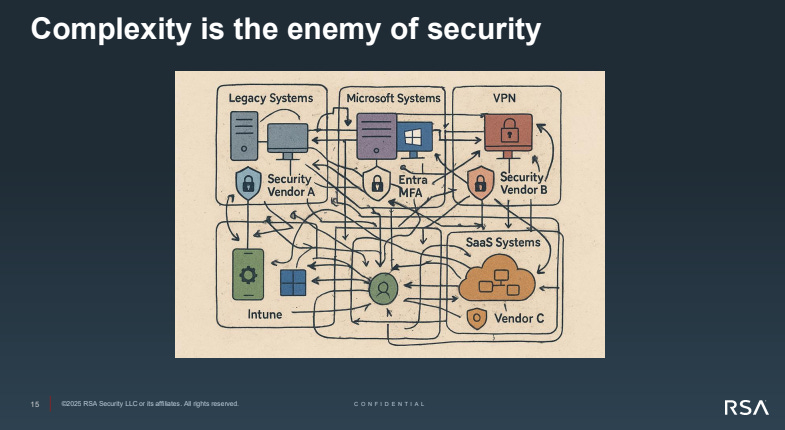
Zohny made a good point about complexity “is the enemy of security”. We can only protect what we can see - and in turn apply critical controls and response processes that cover a range of integrated systems. Even with a selection of core IAM capabilities such as IDPs, MFA, PAM and IGA, disconnections exist and data flows are not properly understood. To that end, visibility is an issue. He argued that RSA is in a position to be the glue to help manage and consolidate this broad array of IAM components.
Orchestration and integration appeared in Pedro Cheganças presentation for AuthCube. A Brazilian vendor focused on B2C, he articulated the need for improved overlay and management for a suite of components that help improve security, reduce fraud but also enhance user experience - which is key of course for retail, finance and telco transactions online and across mobile.
Roger Ingegneri from Sailpoint did a talk focusing on the potential new battleground in identity governance and administration - that of application onboarding and management. IGA is only as strong as the systems under management and getting more applications into the IGA framework as possible can only improve productivity and security and also reduce risk and compliance exposure.
Ungoverned applications are a huge management and security concern and Sailpoint believe their use of AI to help identify, classify and onboard applications can perform this process faster and more accurately.
Ping’s David Gomez discussed fraud and how the use of contextual access can reduce this. He discussed a concept that has been around for a number of years and now available in both the former-ForgeRock and Ping access management components - that of being able to set OIDC and OAuth2 exp (expiration) values dynamically. This was traditionally a static value, but is now a more flexible setting based on authentication or risk settings picked up during consent flows. He argued this improves security but also delivers a more granular and focused user experience.
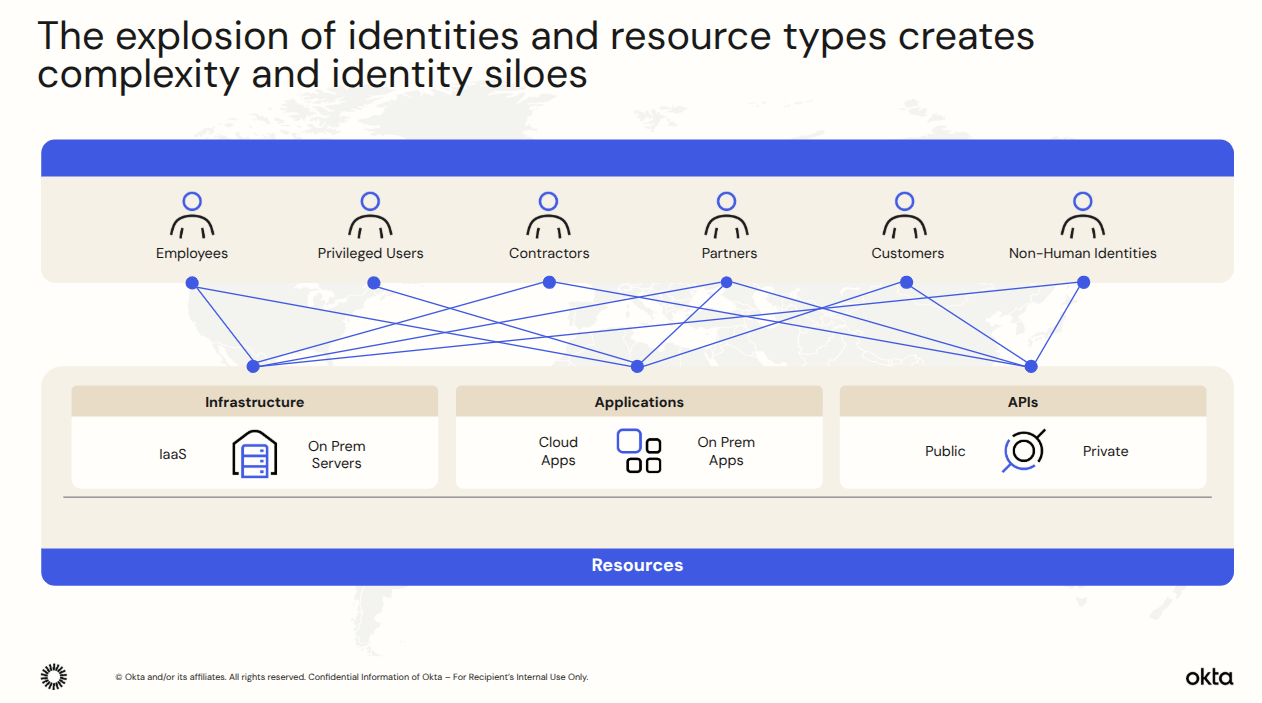
Nuno Silveiro from Okta focused on AI. He argued that the explosion in both volume and types of identities is creating complexity and silo’s that adversaries can exploit.
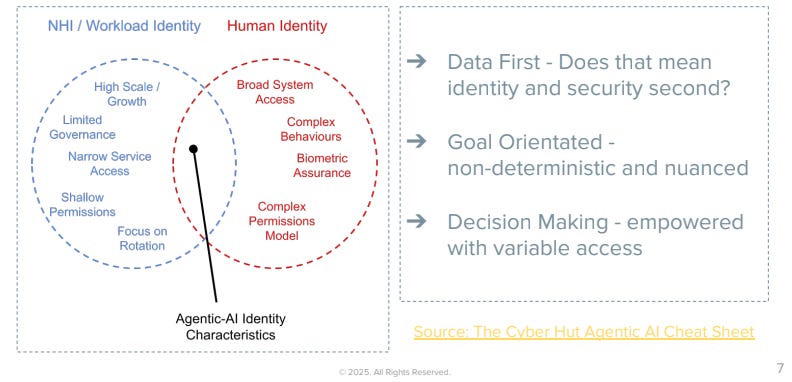
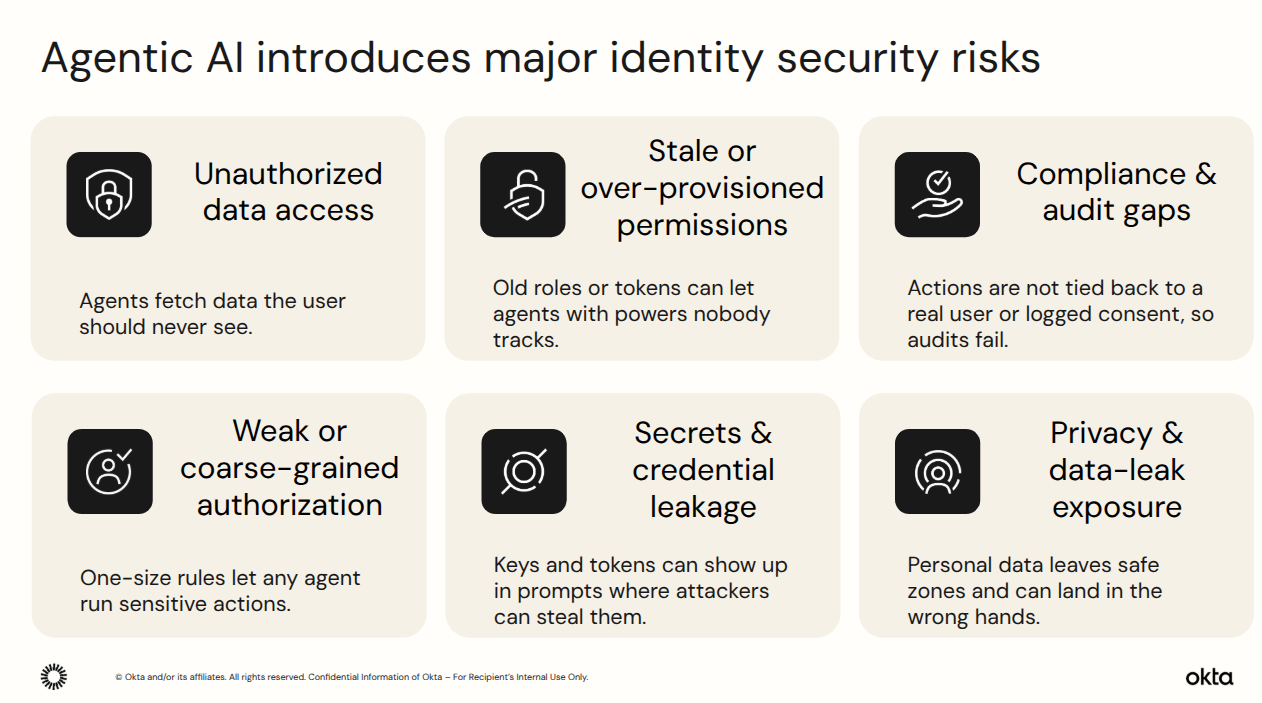
The rise of Agentic-AI is amplifying this concern, with many agent activities “invisible” to core IAM functions.
The answer from Okta’s point of view is being able to apply authn, authz and token management functions to this new and broad array of AI functions. He argued the need for a more end to end life cycle approach for agents, including discovery, registration, authorization and monitoring.
Filipi Pires - founder of B sides Porto - gave an insightful talk taking a look at access path analytics - specifically in the context of machine identities. Again the concept of life cycle management emerged, with a need not only to create inventories and improve visibility of machine identities, but also understand what they are doing - through a 3-point plan of Discovery, Governance and Automation.
Discovery needs to scan code pipelines, static repositories and containers to firstly understand where machine and non-human identities are located. Secondly, controls, policies and enforcement helps improve the security posture and protect the life cycles. Finally automation helps provide a consistent secure running-state focused on just in time access, automated provisioning and de-provisioning of credentials and access as well as the necessary rotation steps based on risk.
The rise of cloud (from cloud service providers to SaaS) has hugely complicated this area though, with mis-configuration a big issue - with 10’s of thousands of permission combinations alone for the likes of Azure, AWS and GCP environments.
About The Author
Simon Moffatt has nearly 25 years experience in IAM, cyber and identity security. He is founder of The Cyber Hut - a specialist research and advisory firm based out of the UK. He is author of CIAM Design Fundamentals and IAM at 2035: A Future Guide to Identity Security. He is a Fellow of the Chartered Institute of Information Security, a regular keynote speaker and a strategic advisor to entities in the public and private sectors.
Download Latest Capability Report Covering 120+ Identity Vendors