Review of The Identity Underground Summit 2025
A specialist practitioner-only community
The Identity Underground community of identity and security practitioners had their inaugural in person summit this week in Denver, Colorado. I was fortunate to have been invited to keynote the days first talk and host a panel with esteemed technology finance guru’s Mark Kraynak Founding Partner at Acrew Capital and Mike Gregoire Partner and Co-founder at Brighton Park Capital.
The Identity Underground is primarily focused upon developing a specialist and member-led focus on providing a safe-space to tackle some of today’s complex identity and identity security issues. From architecture, emerging use cases and vendor discussions, to hiring, budget and metrics - enabling the community is the key.
My keynote tackled the question I hear many times during inquiry and advisory: where is identity and access management heading to? What should I be worried about? Which vendors should I be researching and engaging? My approach as always is to not explain what to think, more how to think about tomorrow’s identity problems and solutions.
The main issue of course, is that IAM has become more important over the past decade. We have more identities to manage, different types of identities, a broader array of systems to protect all to be deployed across on-prem, cloud-native and SaaS ecosystems. We need better ways of measuring IAM investment and success as well as satisfying a broader ecosystem of stakeholders - from data, network and endpoint security teams, digital and app owners, enterprise architecture and compliance.
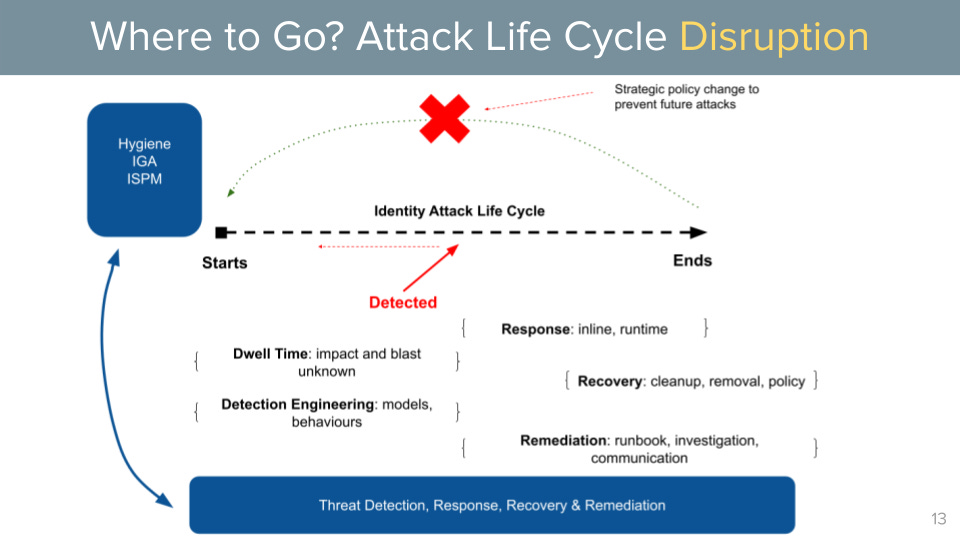
However this is complicated by the fact that identity, is the number one attack vector for both internal and external adversarial activity. Stolen credentials, privilege escalation, session theft, impersonation and fraud all rely on visibility blind spots, poor identity data hygiene and a lack of monitoring.
We need to move away from waiting until events are in the logs - and detect and respond to attacks before they complete.
This will require new approaches to managing identity data (profiles, permissions and policies) as well as understanding more about attribution and intention - with an ability to handle this for both human and non-human identities.
We are already seeing significant movements in these areas with vendors adding capabilities in order to improve identity governance and administration, identity security posture management and identity threat detection and response.
In the NHI space we have rapidly moved away from just discovering where and what workloads we have to manage, to being able to classify, risk assess and apply fine grained controls and responses. The continual adoption and augmentation of next generation PAM, monitoring and automated controls for workloads and NHI will spill over into the management of agentic-AI too.
Daniel Cohen, Pat Buffolino and Kevin Cotter from Paramount gave a fascinating insight into the overlay between identity and security within their organisation. They described how both the cyber security engineering and identity operations worlds are becoming more closely aligned with continual iteration and integration. A great point was made about how to get upper-level management buy-in for identity and access management change such as pushing for the adoption of passwordless authentication. They argued it was essential to “sell” the message upwards, with a focus upon improved user experience and productivity. Regulation of course is always in the conversation an needs to be used a “stick” to promote change.
Fellow analyst Francis Odum from SACR (see The Analyst Brief episode 62 for a mashup conversation between myself, Francis and co-host David Mahdi) facilitated a discussion around non-human identity with Steven Rennick lead IAM architect at Ciena. A quick room poll showed that the term machine identity has been replaced by NHI. Francis brought up the point that the multiplicity of NHI volume, variety of authentication techniques and the management tools (like vaults) to support this is causing management and visibility issues. A new wave of vendors are clearly emerging to specifically tackle this - and whilst using the same concepts from the human-world such as governance, authentication, authorization, just in time access and monitoring - the deployed approaches will vary hugely from the tools we use for the human world.
A innovation panel consisting of Hed Kovetz CEO at Silverfort, Mark McClain CEO at Sailpoint and Peter Barker CPO at Ping brought some interesting points about accountability. We need to have accountability at all levels of our identity world - from permissions and groups to workloads and service accounts. This mirrors exactly what law #3 of the Laws of Identity Security is trying to promote. Of course AI was mentioned and the rise of shadow systems is something that needs to be discovered and controlled. Agentic-AI will bring some interesting challenges - namely around difficulties replicating biometric authentication - but on the flip side, agents don’t suffer fatigue like humans and user experience is not an issue.
Some excellent break out sessions where then built into the agenda, which allowed participants to focus in on some critical topics emerging within our industry. These breakouts were essentially run using Chatham House rules with free-form discussion being used to discuss things like agentic-AI authorization and impersonation use cases, as well a second topic taking a look at employee fraud and onboarding security.
The afternoon concluded with the “Identity Wall of Pain” - a humorous rapid-fire set of speed talks taking a look at some identity pains that have occurred within industry - from accidental offboarding of IT staff accounts to automation gone-bad.