Industry Webinar: Towards Building a Continuous Identity Strategy
Why static design of concepts like joiner-mover-leaver need revisiting
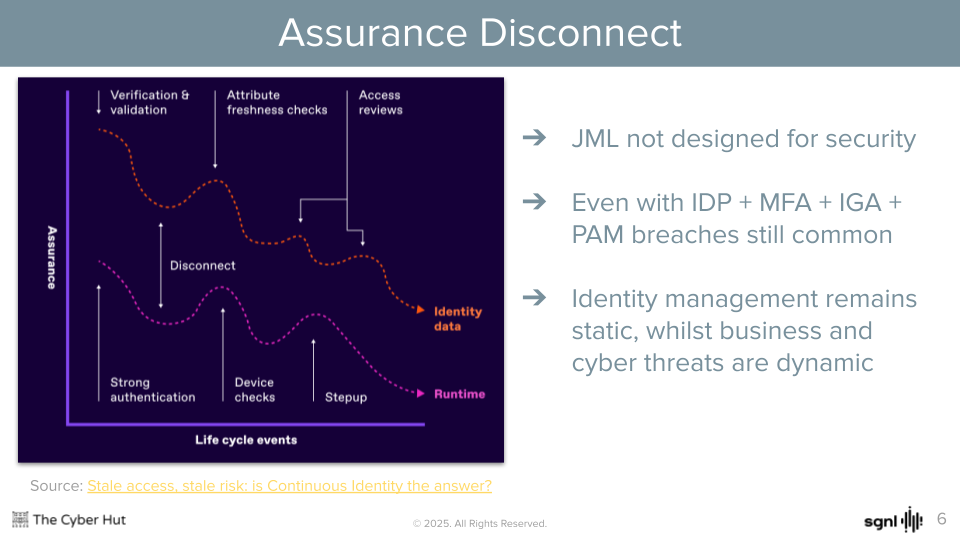
The joiner-mover-leaver process was not built for security. It was built for productivity - with a pinch of compliance too. However it has now become a top target for adversarial activity - from employee fraud, privileged abuse and escalation to lateral movement due to excessive permissions.
JML processes are just one example of the legacy nature of designing in static, often waterfall methods that result in identity information flows that are fragile and unable to respond to external change - be that business or threat related.
If we consider both the data and runtime aspects of the identity life cycle (and that life cycle should be considered for humans, non-humans and the emerging agentic-AI world too) we can see multiple examples where static controls provide some assurance benefits - but they are often short lived and degrading. Strong on-boarding events don’t always translate to strong authentication assurance due to poor credential issuance or reset processes.
Access request and reviews processes provide limited and scoped improvements to permissions assurance - but are becoming difficult to scale and sustain to large numbers of applications and services.
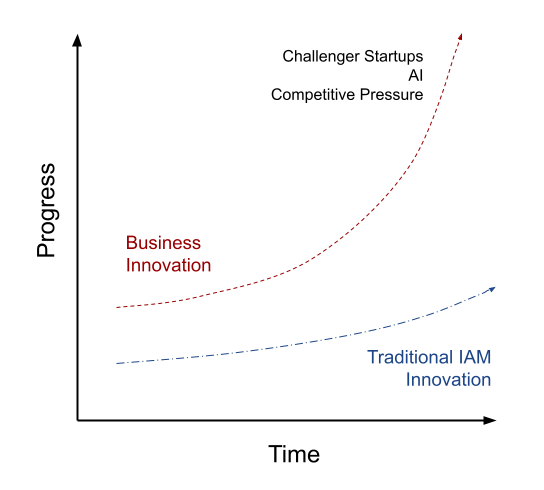
To that end, the static and one-off nature of controls applied to the data and runtime aspects of our identity ecosystems, are being left behind, by the speed of business innovation.
There is considerable risk that the speed of change required by today’s modern enterprise - to support competitor pressure, AI and other - is not being supported by the legacy and isolated pillars of both identity and access management technology and the security controls being applied to them. The greater the gap between the two, the greater the risk of not only business stagnation but an inability to deliver services and applications at pace, and an inability to respond to internal and external cyber threat.
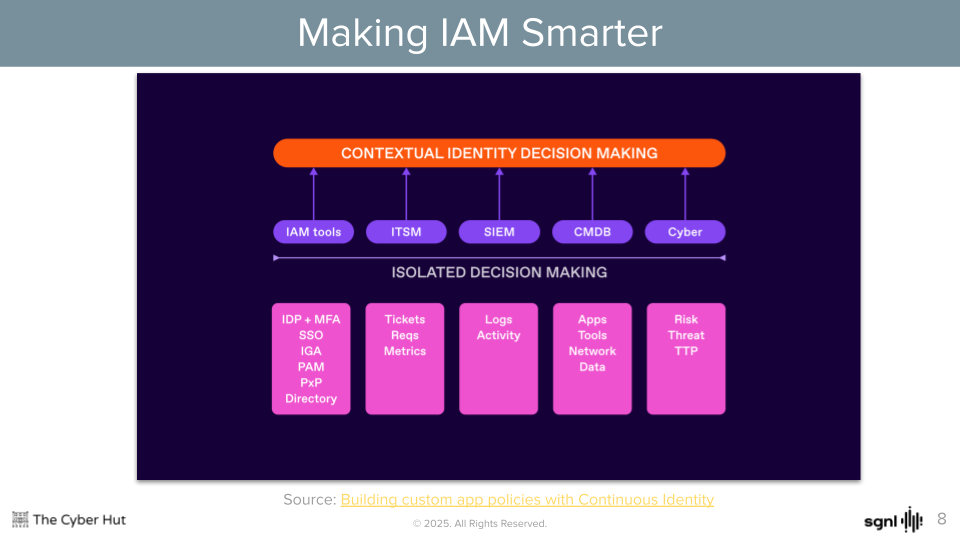
It is becoming increasingly clear, that IAM needs to become smarter. Smarter from a data integration point of view, but also smarter from a response perspective. An ability to both consume and generate risk data that can be fully integrated into all parts of the identity life cycle is now becoming essential in order to allow IAM components to grow at speed in line with business technology needs.
This could include device data being consumed by an identity provider being used for staff authentication, threat intelligence signals by a policy decision point or application activity data to other session validation services. By designing for a more continuously responsive identity fabric both the assurance and innovation gap can be closed to allow IAM to become more closely aligned to key business requirements.
These areas of investigation will form the basis of The Cyber Hut’s next industry webinar which will be taking place on Nov 18th. The Cyber Hut’s founder Simon Moffatt will be in conversation with Mat Hamlin of SGNL, where they’ll discuss the failures driving the need for change, the benefits this will bring and how organisations can get there.
Webinar Details:
Traditional identity and access management wasn’t built for today’s dynamic business environment. Point-in-time security checks and static joiner-mover-leaver processes leave organizations vulnerable to evolving cyber threats, while standing privileges create persistent exposure.
Join Simon Moffatt, Founder of The Cyber Hut, and industry veteran Mat Hamlin from SGNL for an engaging fireside chat exploring how Continuous Identity transforms IAM from reactive to proactive. Discover how leading enterprises are moving beyond stale access reviews and isolated security controls to achieve real-time trust through contextual decision-making, dynamic response capabilities, and end-to-end assurance.We’ll explore practical approaches to identifying standing access, measuring impact, and expanding Continuous Identity across both human and non-human identities. Whether you’re managing a complex hybrid environment or looking to modernize your IAM strategy, this conversation will provide actionable insights for building an always-aware identity fabric that keeps pace with business agility demands.