Why We Need to Shift Left of Boom in Identity
Getting ahead of identity attacks is the only strategic answer
Identity is the new perimeter: it is also the primary attack vector for both internal and external adversarial attacks. From stolen credentials, privilege escalation and misuse, to lateral movement, data ex-filtration and command and communication connectivity, IAM is involved at every stage.
As identity in general, has moved from being a tactical component focused upon employee productivity and compliance, to being a strategic enabler, with that change in responsibility comes increased attention. Budget yes. Different stakeholder engagement, yes. Improved visibility and metrics, also yes. But as IAM now empowers productivity, security, revenue and compliance, with it too comes increasing adversarial activity.
Many organisations have invested upon the main pillars of identity:
Identity Providers, single sign on and multi-factor authentication
Identity Governance and Administration, hygiene, compliance and reporting
Privileged Access Management and high risk identity management
External Authorization using the typical PxP model with policy
Service and workload management and credential automation
Couple with that a range of orthogonal technologies such as data loss prevention, secure access service edge and next-generation software defined networking, endpoint detection and response and integrated logging. All of which I will add are heavily reliant upon and integrated against the identity fabric.
Yet, organisations are being breached daily, even with a highly sophisticated and expensive set of software capabilities. What is going wrong?
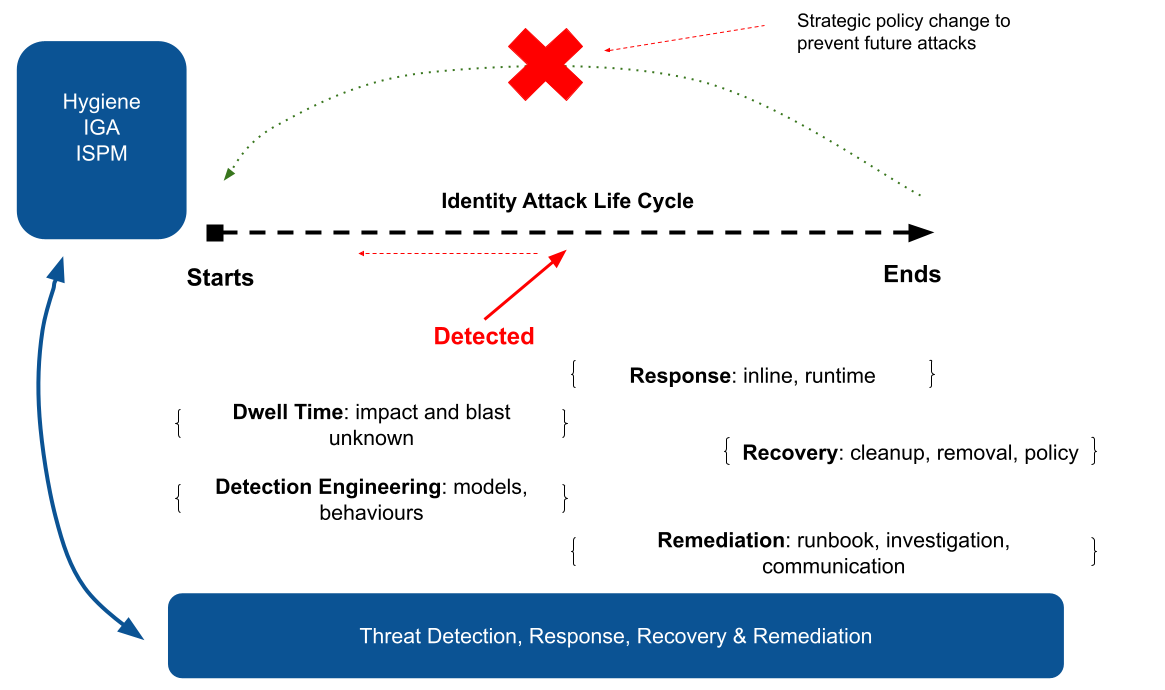
Essentially we have spent a lot of time picking over attacks after they have happened. Security operations, forensics and log analytics are often caught in the post-breach world looking at what has already been and gone. Piecing together identity and access journeys and flows. Tying together identity provider and application activity events, along with network activity. This is perfectly sensible strategy and essential during DFIR and post-event understanding.
But as an industry we have to do more. We have to start getting in front of identity attacks before they complete. Before they steal intellectual property. Before the they render entire departments useless due to ransomware. Before they leak credentials to initial access brokers for future partner attacks.
In a recent article for Reveal Security, I articulate this concept and how we need to “shift left of boom”. Getting a head of the attack, responding and getting fine grained degradation steps in place to stop the attack blossoming into some more significant.
“Ultimately we are aiming to materially impact the mean time to detection (MTTD) and mean time to recovery (MTTR) metrics associated with the attack chain which allows organisations to strategically move to a pre-emptive attack posture.”
Reveal deliver a platform that amplifies the analysis post-login. So taking a look at what happens post-authentication - tackling the session management and enterprise application activity problem by linking activities across-app.
Using machine-learning they aim to identify composite risk across the application stack and not just at the initial login stage.
“Isolated endpoint, network and single-system monitoring using specific rules and “tripwires” are vastly redundant in this identity-centric world. The rise of AI as both an adversarial tool, but also an unmanaged productivity enabler opens up new attack vectors where identity and access management vulnerabilities are exploitable.”
About The Author
Simon Moffatt has nearly 25 years experience in IAM, cyber and identity security. He is founder of The Cyber Hut - a specialist research and advisory firm based out of the UK. He is author of CIAM Design Fundamentals and IAM at 2035: A Future Guide to Identity Security. He is a Fellow of the Chartered Institute of Information Security, a regular keynote speaker and a strategic advisor to entities in the public and private sectors.