Aembit JiT for Workloads, AI for Access, JumpCloud + Breez, OPA to AWS Verified Permissions
This Weeks Mystical Quartet
Curated Industry Headlines
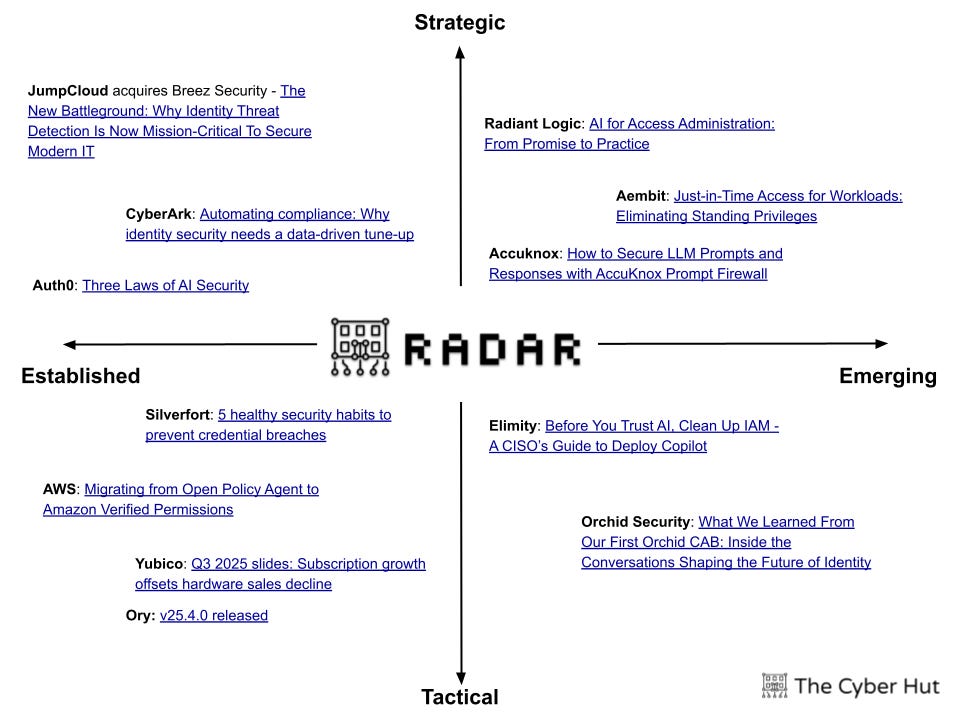
Accuknox: How to Secure LLM Prompts and Responses with AccuKnox Prompt Firewall
Aembit: Just-in-Time Access for Workloads: Eliminating Standing Privileges
Auth0: Three Laws of AI Security
AWS: Migrating from Open Policy Agent to Amazon Verified Permissions
CyberArk: Automating compliance: Why identity security needs a data-driven tune-up
Elimity: Before You Trust AI, Clean Up IAM - A CISO’s Guide to Deploy Copilot
JumpCloud acquires Breez Security - The New Battleground: Why Identity Threat Detection Is Now Mission-Critical To Secure Modern IT
Orchid Security: What We Learned From Our First Orchid CAB: Inside the Conversations Shaping the Future of Identity
Ory: v25.4.0 released
Radiant Logic: AI for Access Administration: From Promise to Practice
Silverfort: 5 healthy security habits to prevent credential breaches
Yubico: Q3 2025 slides: Subscription growth offsets hardware sales decline
Identity Threat Intelligence Updates
Kerberoasting: How a TGS ticket can crack your service accounts
Abusing Delegation with Impacket (Part 1): Unconstrained Delegation
Up Coming Event Attendance:
Chartered Institute of Information Security Live - London - Nov 25th
Blackhat EMEA - London - Dec 10/11
Free Identity Security Cheat Sheets
Cheat Sheet: Top 30 IAM Metrics for B2C
Cheat Sheet: Top Metrics for B2E IAM
Cheat Sheet: MCP Security
Cheat Sheet: Agentic-AI Identity Security
Recent Content
Why PAM Needs to Evolve
A deep dive interview with P0 Security CEO Shashwat Sehgal on the evolution of privileged access, the creation of identity data lakes and how to solve the ever growing issue of more identities and more systems.
Recent Industry Webinar:
17 September - Detect, Protect and Defend: A Holistic Approach to Human and Non-Human Identity Security with Permiso
Recent Podcasts
E64 The Analyst Brief: The Growing Impact of Digital Dependency
Recent Research Reports:
The Cyber Hut: A Market Guide to Identity Security Posture Management (ISPM): The Role of Data-Centric Identity Observability
Recent Insight and Comment:
Stale access, stale risk: is Continuous Identity the answer?
Comment on the role of IAM in Operational Technology for Industrial Cyber magazine
Recent Industry Webinars
Addressing the IAM Data Problem: A fireside chat with Radiant Logic
An Identity Security Playbook: The What and The Why with Silverfort
Putting the AI in IAM a fireside chat with Apono
Recent Academy Episodes:
34: What is SPIFFE?
Recent Vendor Assessment Reports:
Recent Vendor Introduction Interviews:
Recent Video Shorts:
Order IAM and Identity Security Books on Amazon:
IAM at 2035: A Future Guide to Identity Security - Paperback, Audio, Kindle and Hardback
CIAM Design Fundamentals - Paperback, Audio and Kindle